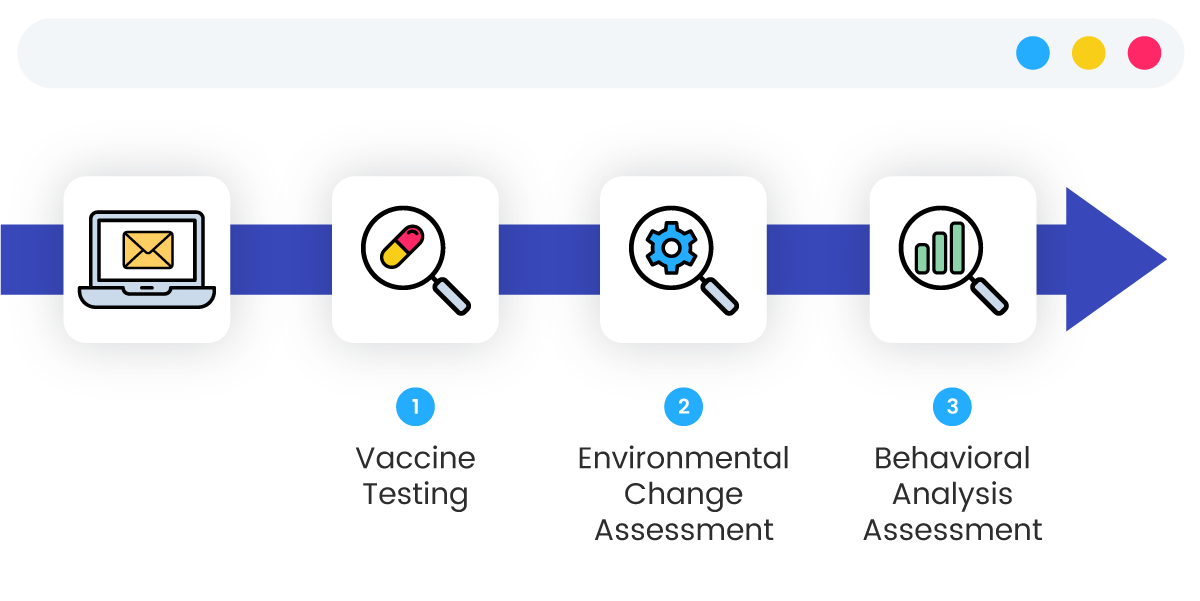
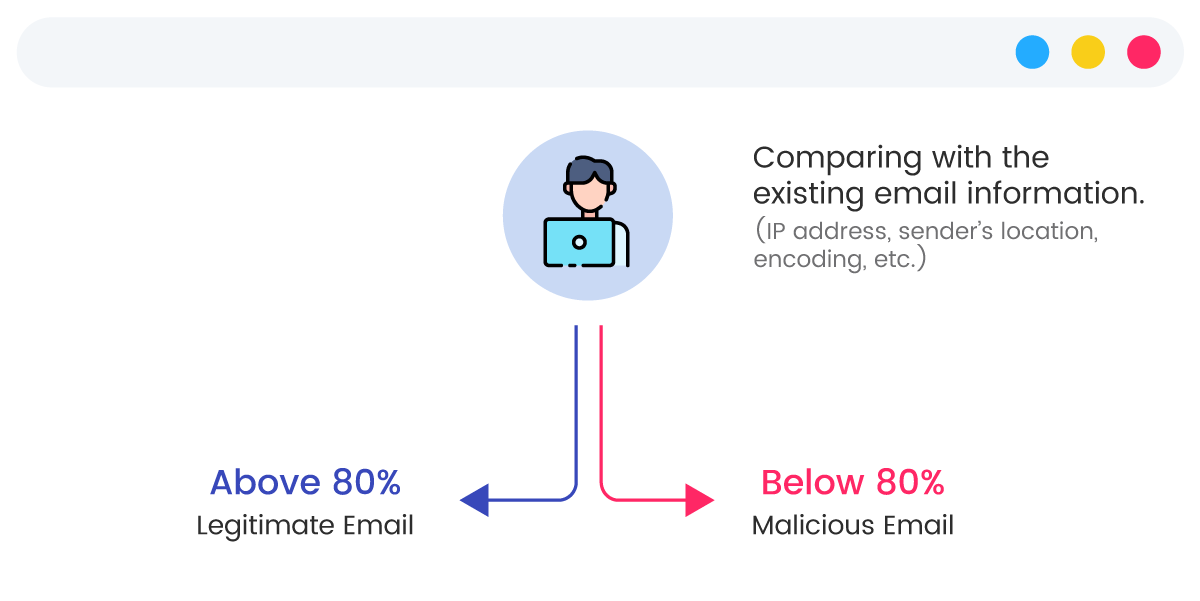
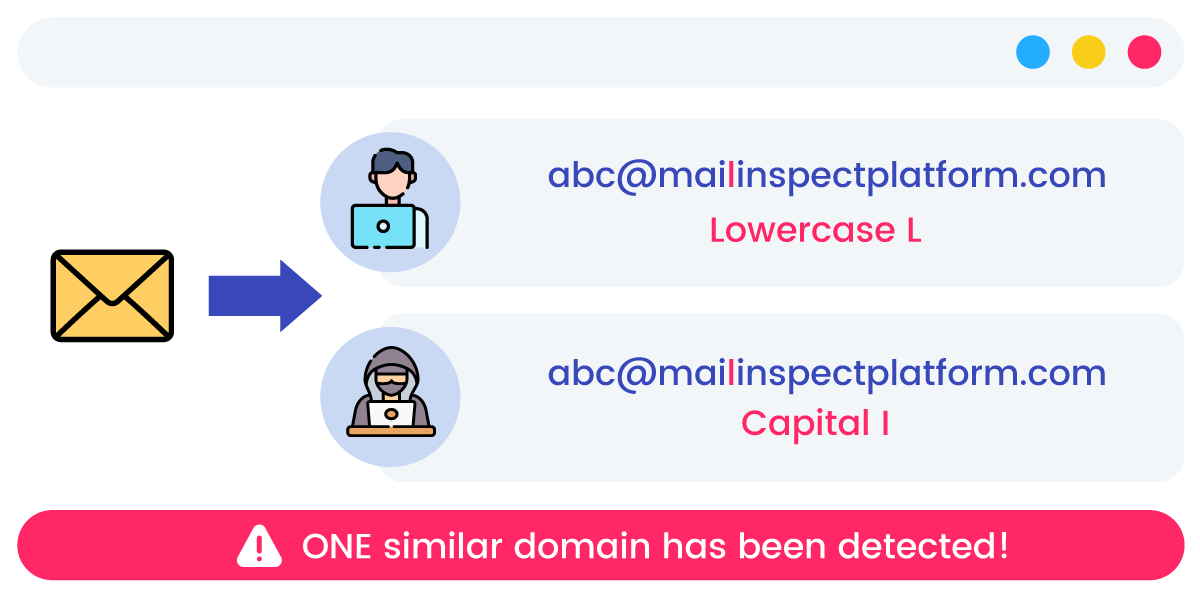
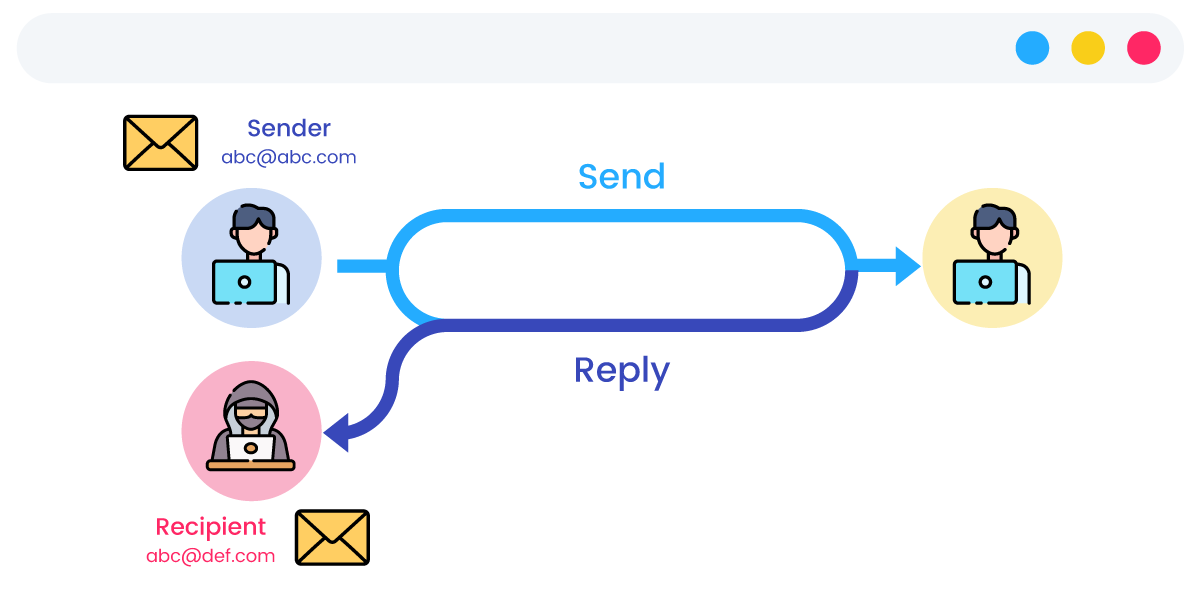
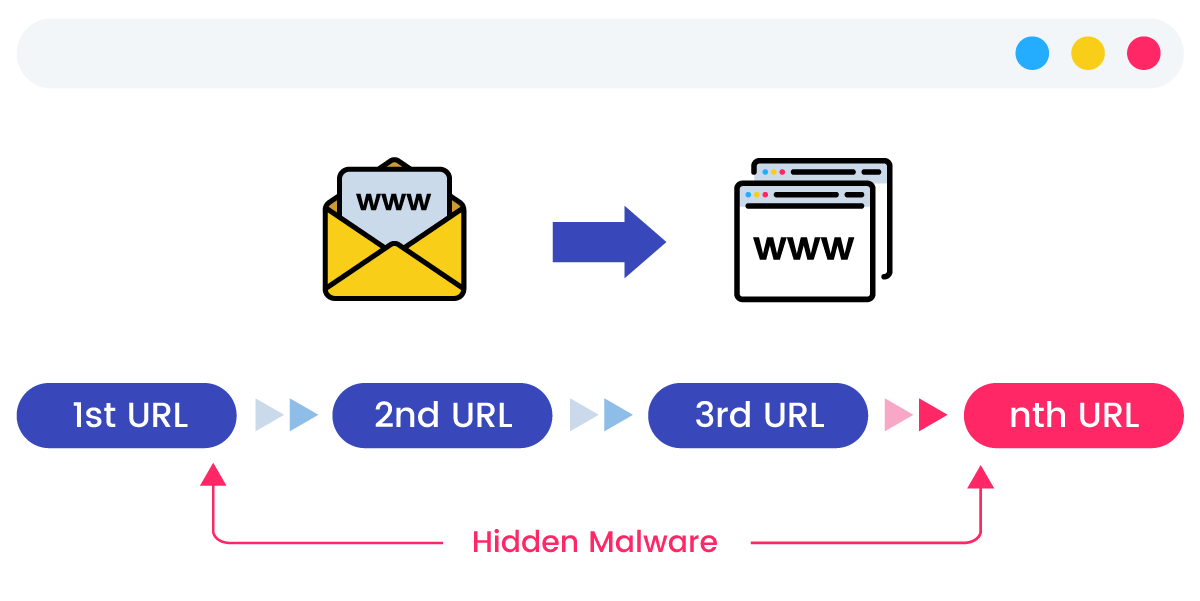
An intelligent preemptive response solution for scam emails that blocks 17 types of targeted email attacks outlined in international standards, which detects a wide range of threats, including emerging malware, similar domain fraud, tracing sender paths, and checking for altered reply addresses.